







- Home
- BUG SWEEPS
- SEARCH MEATHODS
- WHY US
- SERVICES
-
PRODUCTS
 The Search ProcessCONTACT US
The Search ProcessCONTACT US
info@technicalprotection.co.uk
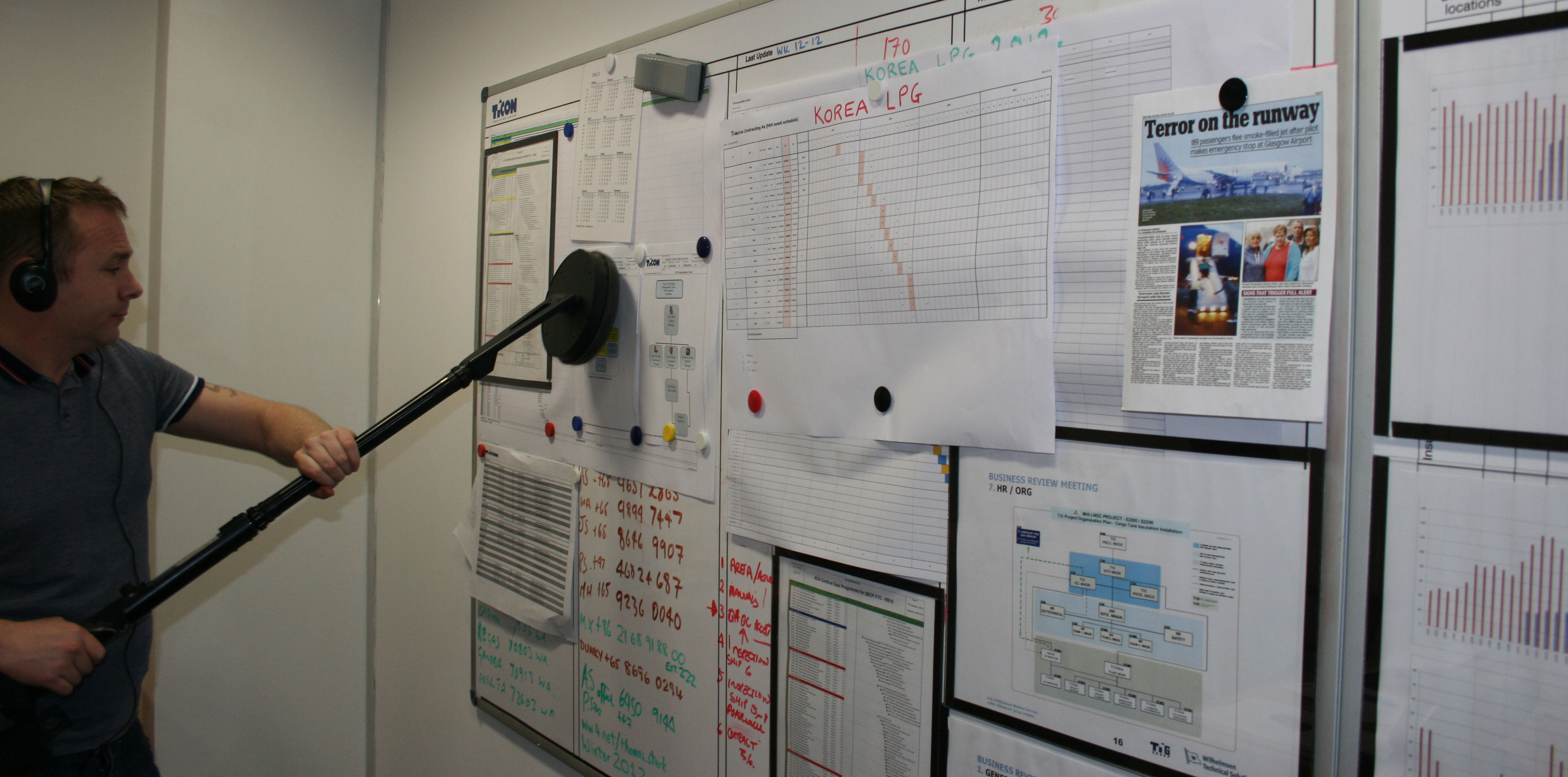
0207 781 9247Our engineers are skilled in telecoms, electronic engineering and software engineering and are experienced in countering such threats. Our operatives are fully qualified to advise on all types of information security and methods to counter electronic eavesdropping.Depending on the area of the premises to be searched, our dedicated search team will consist of one to twelve engineers. All our specialists have at least 8 years’ experience in security sweeping.OUR SPECIALISED COUNTER SURVEILLANCE TEAM· GSM MOBILE THREATS· VOIP, PHONE NETWORK & EXCHANGE INTEGRITY· BLUE TOOTH, NEAR-FIELD & WIFI NETWORKS ACCESS & SECURITY· RF (RADIO FREQUENCY) Frequency Hoppers, Burst transmitters etc· PHYSICAL & OPTICAL· FIBRE OPTIC MICS· TELEPHONE INTERCEPTION· VIDEO SURVEILLANCE· SOFTWARE AND HARDWARE KEY LOGGING· LASER AND INFA-RED ATTACKSThe Process: Given a few details, our team create an initial brief, quickly assessing the type and nature of any surveillance threats facing the client, whether the threat is of an individual nature, a company or group. Our team utilises an array of cutting edge TSCM solutions specifically designed to address each area of risk: these threats include, but are not limited to:As one of the leading TSCM search teams in the country, we offer a range of services at local and national level in the UK and overseas. Below is a very brief introduction to the process required for a TSCM search, or as it is more commonly known, bug detection. If you are concerned about any security issues please feel free to contact us immediately.
 0207 781 9247
0207 781 9247